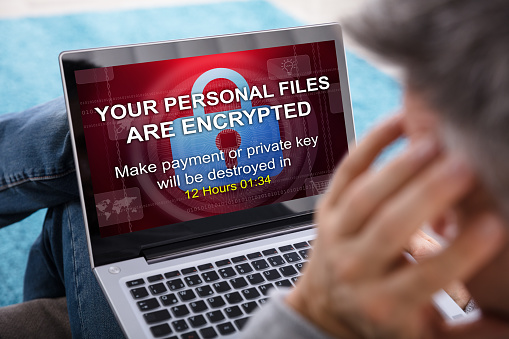
A major FaceTime bug discovered recently has left Apple device users skittish about yet another privacy concern and forced the tech giant to scramble for a fix for the issue.
For users of Macs or iPhones, understanding the FaceTime flaw and knowing how to disable the function are important steps until the issue is fully resolved.
What is the FaceTime Flaw?
The FaceTime flaw affects iPhone users running iOS 12.1 or later. Here’s how it works. Someone calls your number using the FaceTime feature. Before you pick up, the caller swipes up and adds their own number (or any number), creating a Group FaceTime interface.
At that point, the caller can hear all audio coming through your microphone — even if you never answered the call.
News of the glitch spread like wildfire over social media. Others discovered that taking further simple actions could give the caller access to video, too.
What Is Apple Doing About the Issue?
Within hours of broad disclosure of the issue, Apple disabled the servers controlling the Group FaceTime function. As of January 29, Apple’s system status page states that “Group FaceTime is temporarily unavailable.” The company has stated that a fix is likely in a few days.
The company had first introduced Group FaceTime in late 2018 for both Macs and iPhones.
What Should I Do About FaceTime on My Device?
Users may want to disable FaceTime on their iPhones or Mac computers. It’s a simple process for either device type.
For iPhones
1. Go to Settings .
2. Scroll to FaceTime. This feature is in the fifth section of settings along with other built-in apps like Phone, Messages and Maps. If you’re having trouble finding it, go to the top of the Settings screen and type FaceTime in the search bar.
3. Click on the FaceTime bar.
4. At the very top of the FaceTime settings, there’s a label marked FaceTime with a slider. If the green light is lit, FaceTime is activated on your phone. Slide the slider to the left to turn FaceTime off.
Note: When Apple releases an iOS update, install the update, go back to the FaceTime settings and slide the slider to the right to reactivate the feature.
For Macs
1. Launch the FaceTime App.
2. Select the FaceTime menu bar from the top-of-the-screen navigation.
3. Select Turn FaceTime Off. Command-K also turns the feature off.
Note: Once Apple releases a fix, turn the feature back on by launching the app and clicking the Turn On feature.
How Did This Happen?
It’s unclear how this flaw was included in the Group FaceTime release. However, the New York Times reported that a 14-year-old Arizona boy discovered the glitch on January 19, 2019, 9 days before it became widespread on January 28.
On January 20, the boy’s mother sent a video of the flaw to Apple, warning of a “major security flaw.” She heard nothing from Apple Support and began using other channels to try to get the company’s attention. She emailed and faxed information to the Apple security team. She posted alerts to both Twitter and Facebook. Five days later, on January 25, Apple’s product security team suggested she create a developer account and submit a formal bug report.
It appears that the company didn’t react until three days later when a developer reported the flaw and a 9to5mac.com article went viral.
Apple faced criticism for its brief and limited response, which stated the company “identified a fix that will be released in a software update later this week.” In an ironic twist, the bug went viral on January 28, which is international Data Privacy Day.