Cyber attackers are highly motivated to obtain or corrupt your company’s data. But whether their motivation is to steal your funds outright, hold your data for ransom, practice espionage, or simply disrupt your business, most hackers cannot access your network without an “in.”
In other words, they require a login, personal access codes, or network access through malware to initialize their breach. Unfortunately, a recent report released by Verizon has concluded that 93% of the time, a cyber attacker’s “in” comes to them in the form of a social engineering attack on your employees.
The only way to prevent such breaches in your security is with proper cybersecurity training.
What is a social engineering attack?
Social engineering attacks are frankly less high-tech than traditional cyber attacks by highly knowledgeable tech criminals. In other words, they don’t require the extensive knowledge and tools needed to directly hack a highly protected computer system out of nowhere.
Social engineering attacks are more like street scams — only they’re usually done online or sometimes, over the phone. These scams use human psychology to fool individuals into willingly giving up sensitive information. In the case of your business, the targets are your employees.
There are several types of these attacks, including “phishing” and “pretexting,” which are quite similar and often go hand-in-hand. Phishing emails, however, remain the most common type of social engineering scam.
What are phishing emails?
In short, a phishing scam might be an email sent to the employees of your company that looks legitimate. It might (appear to) be from the employee’s bank, for example. It might request that your employee “click here” and login to (what looks like) the bank website so that the bank can “update your information” or “confirm your identity.”
A phishing email might also promise something to the recipient: “Here’s your free 50% off coupon! Click here!” or use a so-called emergency to illicit fear: “Someone has hacked your account. Click here to get it back.”
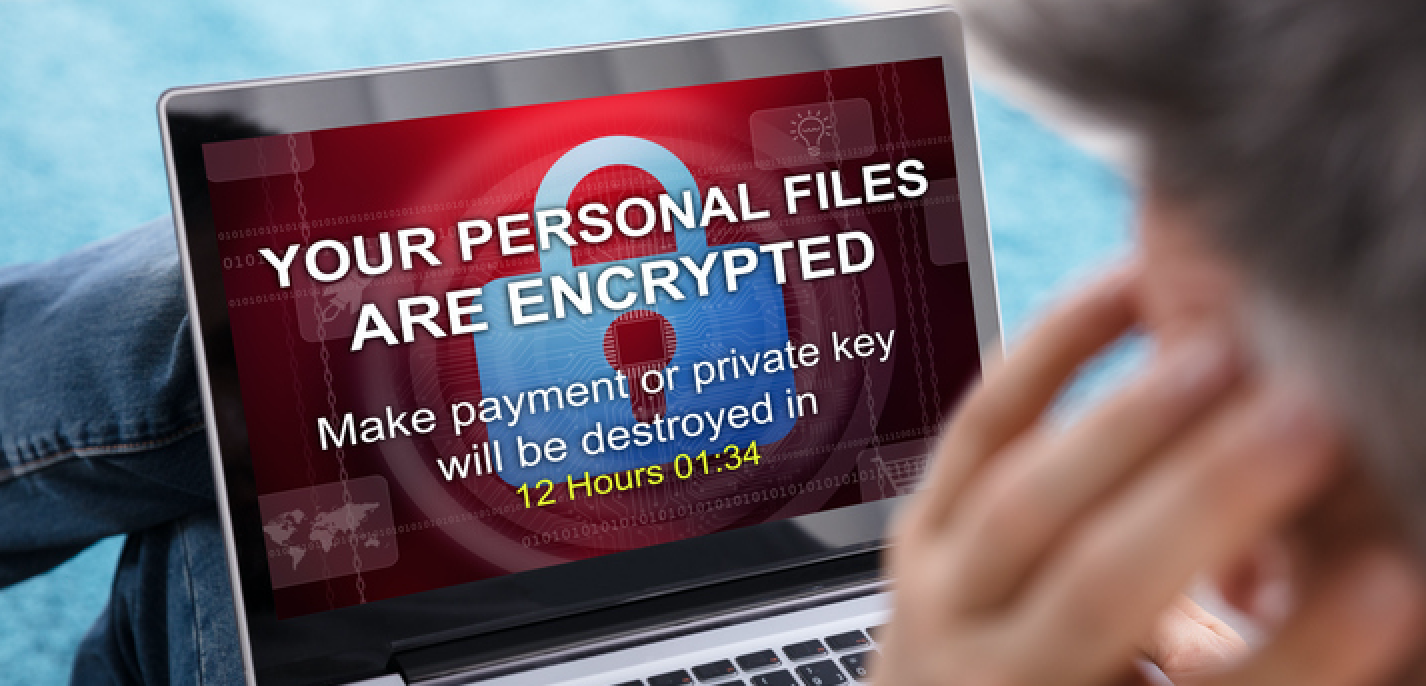
If your employee does indeed click on the malicious link of a phishing email, they will likely be taken to a blank or uninteresting page. In the meantime, however, the link click will have initiated the installation of malware onto the employee’s computer. This malware then enables the hacker to obtain sensitive information or disrupt or damage your company’s data.
How can company’s prevent phishing scams?
The reputational implications of any type of security breach — even one that doesn’t actually corrupt or steal your data or funds — can be enormous. Of course, it goes without saying that if you are caught in the crosshairs of a data ransom or cyber theft, the financial implications will be equally devastating.
As we’ve learned from the Verizon report, most security breaches are linked with phishing. Therefore, cybersecurity training for your employees is the best preventive solution you have for stopping security breaches before they start.
Employee training is not expensive, yet it is highly effective. Your employees should learn the following throughout their ongoing training:
- How to identify a range of phishing and pretexting scams
- How to proceed should they find an email, phone call, or social request suspicious
- Your company’s strict policies and procedures for communication (for example, “We would never send emails requesting personal information from our employees as this would only be done in person.”)
- Notice of increased risks for phishing scams around the holidays
- Notice of the most recent and common scams currently trending
Cybersecurity training should be frequent and come at regular intervals throughout the year as attack strategies often come randomly in spurts and habitually change tactics.
While cybersecurity training is your best line of defense when it comes to phishing and security breaches, it’s also important to hire a reputable IT managed service provider (MSP) to handle your network and security. Your MSP should have experience and broad skill in protecting their clients from network breaches. Contact qualified MSPs in your area today to learn more about protecting your business from cyber attacks.