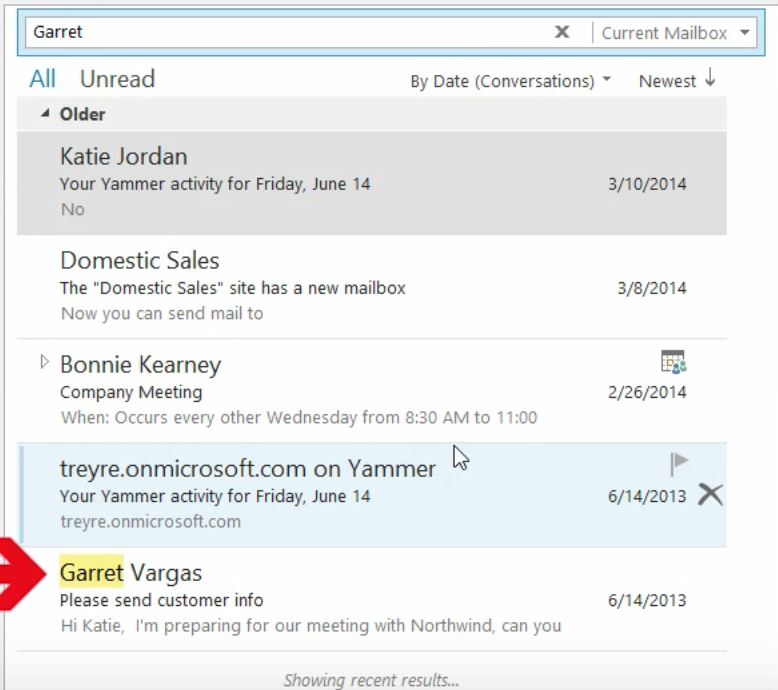
A ransomware attack has left Atlanta officials with no choice but to shut down their municipal courts while they determine the best course of action. The hackers responsible are demanding $51,000 worth of bitcoin in ransom.

In late March, the city of Atlanta’s IT systems were hit by a ransomware attack that is still affecting them today. Described by Atlanta Mayor Keisha Lance Bottoms as a “hostage situation”, the ransomware attack has crippled their municipal court’s IT systems and is preventing residents from paying bills online. The cybercriminals have demanded a ransom of $51, 000 to be paid in bitcoin.
Since the ransomware was first discovered, the city officials, along with members of various law enforcement agencies, such as the FBI and Department of Homeland Security, have been working hard to determine what type of information was compromised and whether it could affect citizens directly.
The SamSam malware in question hunts for critical files and uses AES 256-bit encryption to lock them up, offering a key to decrypt them only if a bitcoin ransom is paid. If the victim doesn’t pay, they erase all the data.
What makes SamSam different is in the way the attacks develop. SamSam scans for open ports and uses a brute force attack until it gets in. A brute force attack means that they’ll constantly hit the port with credentials until one works. Once the hacker group succeeds, they’re inside your system.
The ransom note left by hackers said that refusing to pay the $51,000 would result in deletion of all the information. This particular group of hackers has successfully collected $850,000 since last year.
This wasn’t the first time SamSam paralyzed a government – it also infected offices in Colorado, North Carolina, Alabama, and Maryland. Governments’ operations are mission-critical, and so hackers like this know that they often pay the ransom.
What about your business? Could you wait more than a week after a ransomware attack to start turning your computers back on? How long could you hold out before the loss of business and downtime would cause permanent damage to your bottom line?
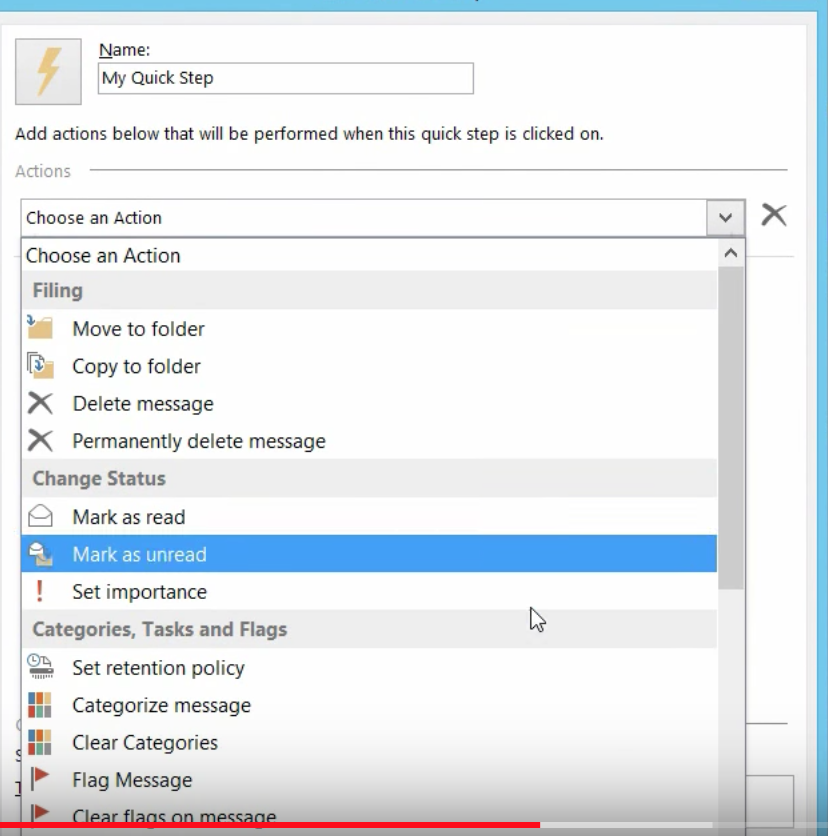
How Ransomware Works and How To Defend Against It
In a ransomware attack, a hacker gains access to an organization’s computer systems. Typically, an unsuspecting employee clicks on an emailed attachment that appears to be a bill or other official document. In actuality, the attachment installs a malicious software program (malware) onto the computer system. Once embedded, the malware allows a hacker access to critical systems, often giving complete remote control data and access.
Hackers are getting more sophisticated. Today, the malicious code may be placed on a website. When a user with an unsecured or unpatched software program accesses the site, the malware slips inside that user’s computer.
Protecting your business
The FBI recommends that organizations continue to be vigilant when it comes to safeguarding systems and educating employees. The two areas that the FBI recommends that organizations focus on are:
- Creating and frequently reviewing a robust business continuity plan that can be deployed in the case of a ransomware attack. Data should be backed up regularly. The backups should be inspected to verify that they maintain their integrity. Backups need to be secured and kept independent from the networks and computers they are backing up.
- Ensuring employees receive proper awareness training and that prevention controls are in place and comprehensive.
Tips for keeping systems secure
The FBI has released the following tips that are applicable to organizations, employees, and individual computer users:
- Be sure that employees understand what ransomware is and what role they play in keeping the organization’s data and computer network systems protected.
- All software, firmware, and operating systems should be patched on desktop and digital devices (including smartphones, tablets, and laptops). A centralized network patch management system can make the coordination of these efforts easier in large organizations.
- Confirm that anti-malware and antivirus settings are deployed to automate all updates and to continually conduct system and device scans.
- Have very clear access and authorization procedures in place. Do not provide administrative access to employees unless absolutely necessary. Administrator accounts should be used sparingly.
- Access controls should be configured so that shared permissions for directories, files, and networks are restricted. The default settings should be “read-only” access to essential files, with limited permissions for write access to critical files and directories.
- Macro scripts in Office files should be disabled when sent over email.
- Software restriction policies should be created or other controls implemented that prevent execution, especially in the common locations where ransomware lurks, such as temporary folders used by the most common web browsers.
The FBI encourages any organizations that believe they have been a victim of a ransomware attack to report the issue to the agency’s Internet Crime Complaint Center.
Don’t wait until a ransomware attack locks up your data. Take steps to protect your business now by partnering with Ray Morgan Company. Get in touch with us at (530) 343-6065 or info@raymorgan.com to get started today.