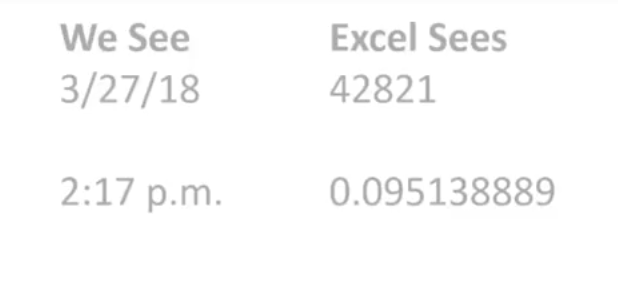
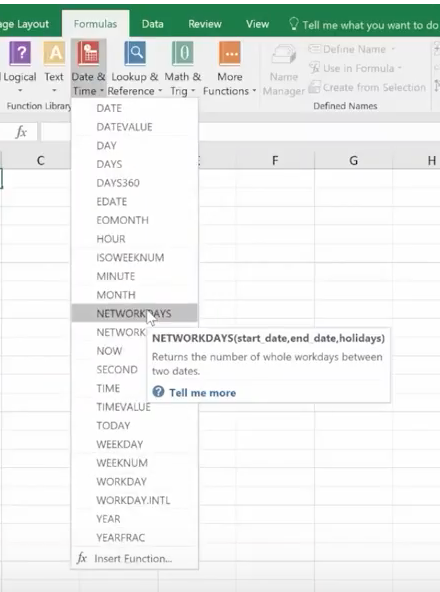
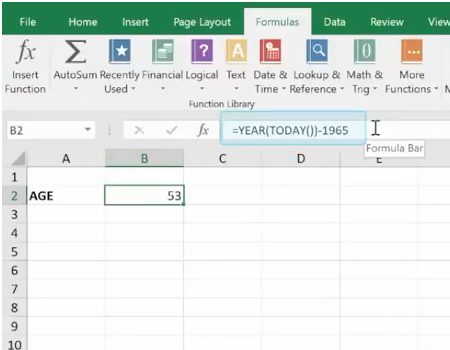
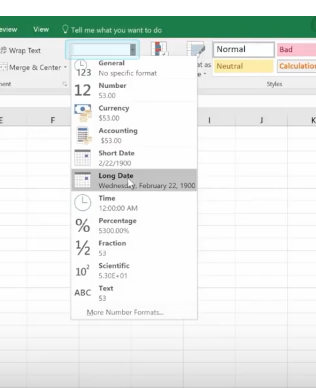
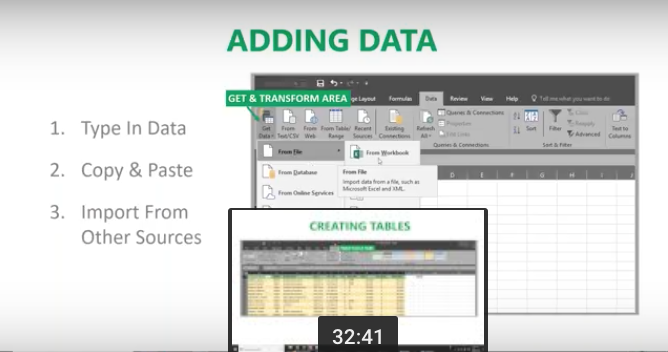
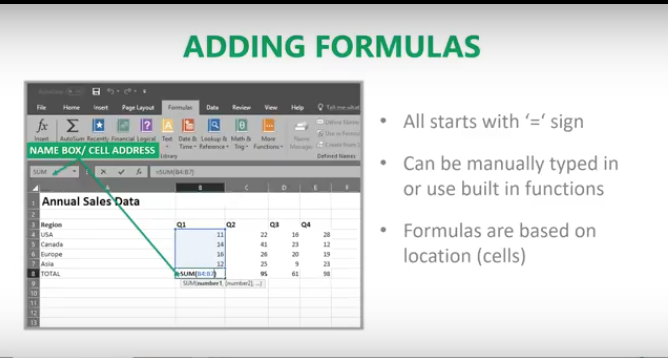
In this age of information, it’s challenging to maintain compliance with so much data stored on many different devices. Most companies these days have remote workers, employees in various departments, third-party vendors, management, employees working in other countries, and more. These people have laptops at home and at work, smartphones, and tablet computers. All this information must be structured in a way that it can be stored or accessed successfully whenever needed. This is a massive task that seems impossible, yet with enterprise content management programs, it’s suddenly doable.

Information Overload
Americans are now overwhelmed with the massive amounts of data that exist in their world. But it’s not enough to have a world full of information available; you must know how to use it to achieve your business goals while adhering to compliance regulations. Though there are many ways to handle these tasks, the key is creating a system that’s user-friendly but safe from hackers. Compliance is all about protecting everyone’s data from the world’s cyber thieves.
Losing Control of Compliance
With so many different methods of storing and maintaining data, it’s easy to lose control of compliance issues. This is a problem for every business owner, large and small. Enterprise organizations are easily the most vulnerable simply for the sheer volume of data they must maintain. Our age of information can loom out of control with the simple act of one employee losing a computer. Suddenly, hundreds of records are at risk and the company is struggling to find out what information has been lost. These types of events occur much more often than most CEOs want to admit.
How ECMs Help
Enterprise content management systems can create a safe method of handling and control all this important data. A few of the solutions include:
- Optimizing workflows using multifunction devices to reduce the number of machines and interfaces
- Improving the security of all documentation
- Ensuring ongoing compliance with industry requirements
- Ensuring the best performance of hardware and software
- Minimizing downtime to cut overall costs
- Implementing green strategies with rules-based printing and cartridge recycling
The latest ECMs utilize additional resources to better manage conference rooms, mail rooms, help desks, procurement and many other areas where productivity can be radically affected. There’s much more to managing content than meets the eye.
Controlling the Data Flow
If you’re running a large business with hundreds or even thousands of employees, these types of issues can be extremely hard to control. Every company needs to achieve an optimal level of productivity. However, a healthy level of compliance has become an important factor in this mix. There’s just too much at stake these days if the personal information of millions of consumers is compromised.
In addition to your company’s internal rules and requirements, you may be forced to observe regulations from:
- The Health Insurance Portability and Accountability Act (HIPAA)
- The Affordable Care Act (ACA)
- The Sarbanes-Oxley Act (SOX)
- The Occupational Safety and Health Act (OSHA)
Audits Can Be Stressful and Expensive
Imagine the IRS showing up at your door and demanding your documentation to prove compliance in some or all of these areas. Where do you even begin? Your employees might have to sort through several data systems, search file cabinets, and reign in multiple records from dozens of computers and other devices. This scenario can be a nightmare that no one wants to endure. Missing paperwork and costly errors are just the beginning.
That’s why so many large companies are moving over to enterprise content management systems. These systems provide an efficient method of storing, tracking and managing large volumes of data. Everything is located in a single repository. This makes it far easier to locate important documents that prove compliance. Plus, important documents are protected from intrusion.
Easing the burden of complying with today’s wide range of regulations can give your company leaders peace of mind. It’s a real confidence boost for the stockholders as well. Using advanced robust technology, your organization can move forward more efficiently with a higher level of security.
Easy Search & Collaboration
The best enterprise content management systems are cost-effective, secure and easy for everyone to use. They support all common platforms and databases. Information should be easy to search with programs that seamlessly send a document to the scanner or printer. Most teams need to be able to collaborate in real and virtual meeting rooms. It can be very helpful to be able to find a document, then edit it live together with other teams. This helps everyone stay informed and up-to-date. Transparency in document editing is also important, especially in the event of an audit.
Maintenance & Certification
Another important element, various filters can determine when regular maintenance on the equipment or data is necessary. Alerts are sent out to the correct employees when they need new certifications. These seemingly small tasks keep things flowing and people on track. Once new certifications are obtained, copies are stored with their expiration dates. These documents are fairly easy for auditors to check and this makes everyone’s life a little simpler.
Greater Security
In the past few years, everyone has been shaken by the enormous number of identities stolen in various data breaches. Security is paramount on everyone’s mind. Rules-based settings can be employed to allow access only to those with proper authorization. When you’re dealing with financial data and health records, you simply can’t be too careful. This data should be available whenever needed but safe from hackers. Many enterprise customers are moving to ECMs simply to improve their security. This has rapidly become an important part of doing business.
Proper Archival Procedures
The government requires certain tax forms to be on file for specific lengths of time. However, most documents will eventually need to be archived. The Department of Labor and IRS have many such requirements. Employees can become confused about the requirements resulting in significant fines. A good enterprise content management system eliminates these worries with automatic purge and archive features. Settings can be altered to meet any specific or preferred criteria.
Growing for the Future
With all these things in mind, search for an enterprise content management system that will grow with your company. In the future, compliance may become even more critical. Companies will certainly continue to expand all over the globe, making compliance even more difficult. If your company incorporates a good ECM from the beginning, these issues can be dealt with as you go along, avoiding any abrupt changes to your daily operations.

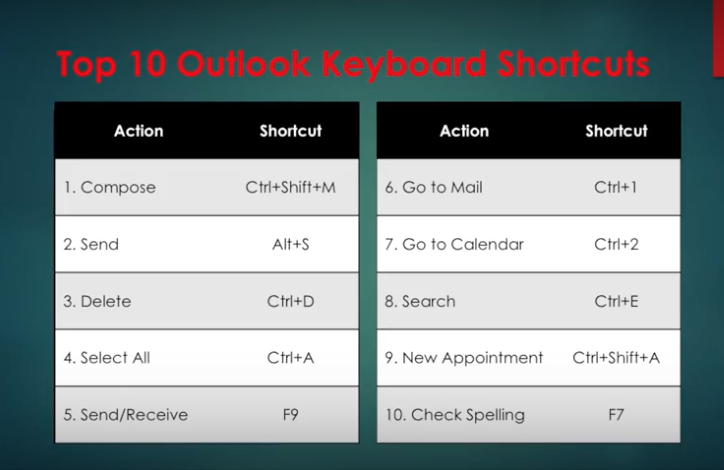
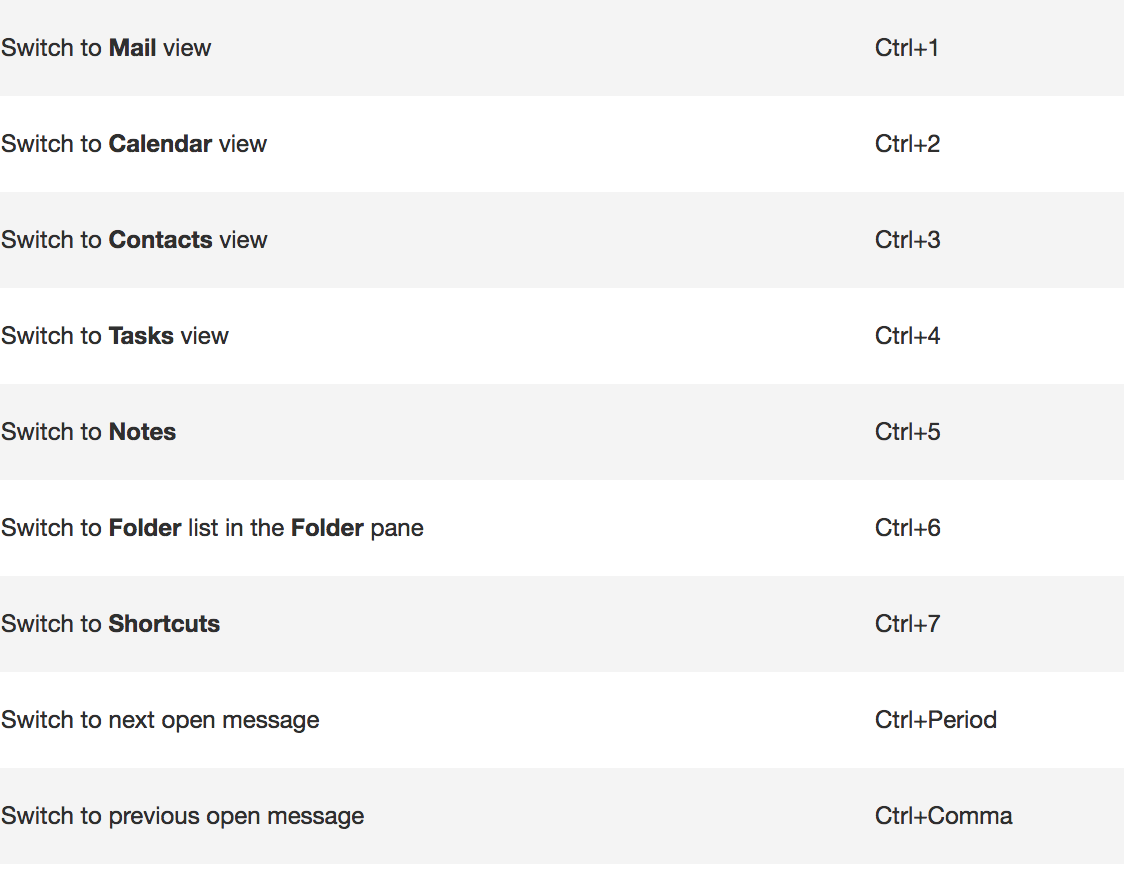
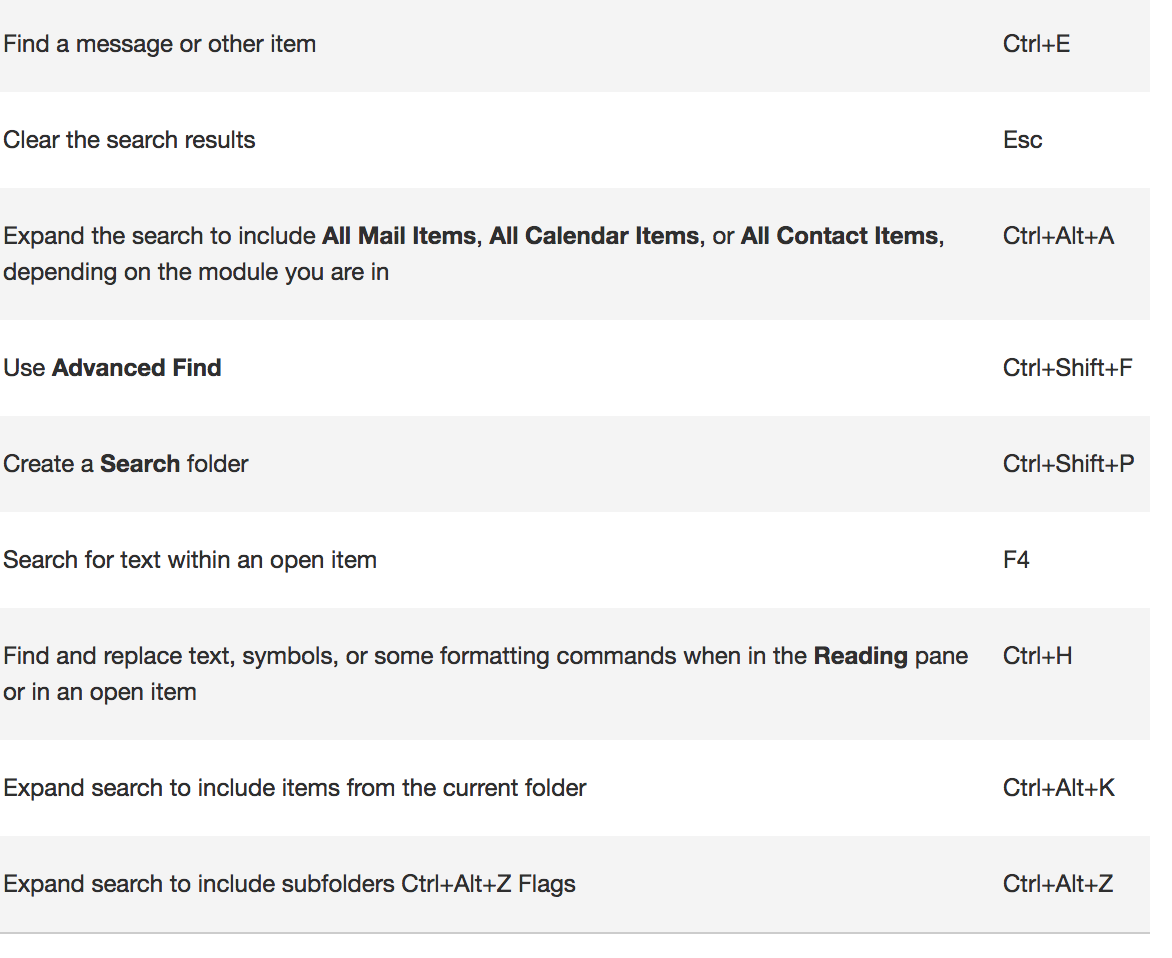






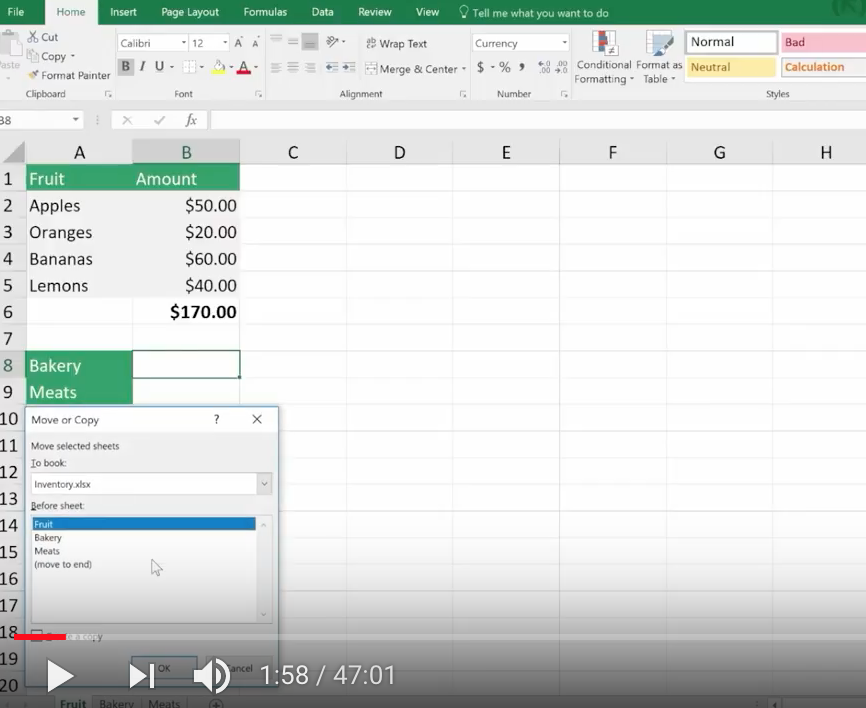
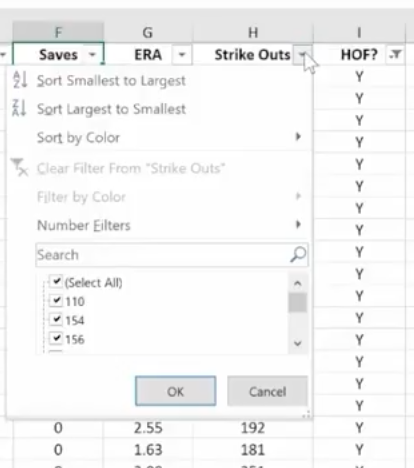
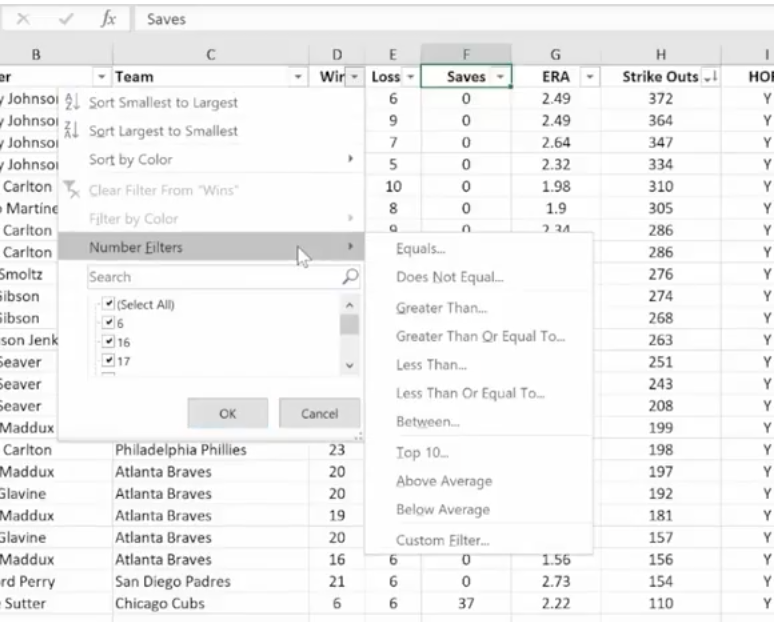
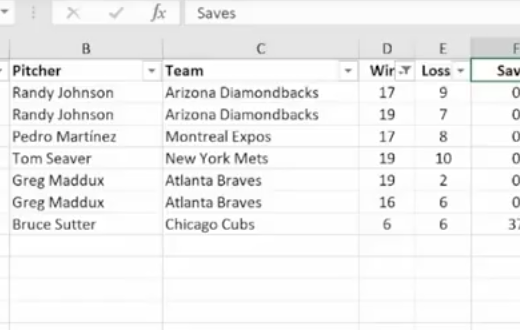
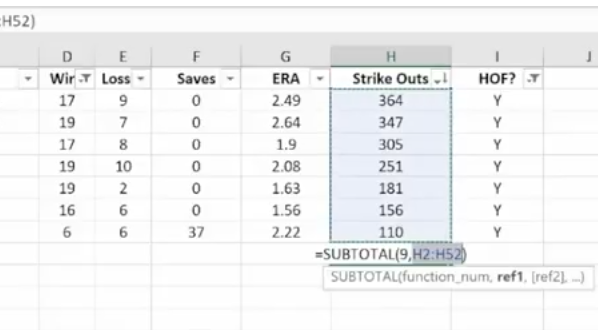
 The Filter Icon is an easy way to see that a column is filtered.
The Filter Icon is an easy way to see that a column is filtered.