Why are Tech Giants Diving into the Health Care Business?

In a report by Christian Holz and Edward Wang of Microsoft Research, the researchers revealed that Microsoft is creating eyeglasses that measure blood pressure. What Microsoft is calling Glabella, the glasses are equipped with optical sensors hidden inside the frame. These sensors can recurrently measure pulse waves at three different locations on the face. By gauging the time and rate between these three areas and the heart, it can determine the user’s blood pressure. Concurrently, the eyewear can be used as an activity tracker as it also collects information on the individual’s physical activity.
Tech Giants Clamoring to Enter the HealthCare World
Microsoft’s newest eyeglass patent arrives on the heels of its rivals. Apple, Google, Amazon, and Samsung have also filed patents for products in the area of healthcare technology. Google has already filed a patent for eyeglasses that monitor heart rate and Apple recently filed a patent application for a monitoring cuff that measures blood pressure. Samsung’s forthcoming new Galaxy Watch is rumored to be able to calculate your heart rate by using polarized light that can identify the amount of the scattered light.
Amazon is working on a new partnership with JPMorgan Chase and Warren Buffett. Apple is building state-of-the-art medical clinics. Google’s umbrella company Alphabet, is entering the Medicaid market with plans to serve low-income urban residents covered by Medicaid and Medicare. Also, studies show that more and more people are opting out of emergency ambulance service in favor of Uber taking them to the hospital.
Why Are these Tech Giants Making Big Health Care Moves?
Why are the most proven and forward-thinking companies in the field of technology deciding that healthcare should be their next big move? With technology rapidly advancing, these tech titans are noticing a health care system full of administrative ineptitudes, out of control prices, and frustrated customers. To the movers and shakers in Silicon Valley, they see this as a huge opportunity to enter the complex world of health care and make it better.
The Pros and Cons of Tech Businesses in the Healthcare Field
Is health care similar to other areas of the economy that Silicon Valley currently manages? Health care is one-sixth of the American economy, and it is currently managed by a scrambled assortment of manufacturers, providers, administrators, payers, and patients. The complex, murky, and massive healthcare industry has many vested players. They aren’t going to stand idly by and allow Silicon Valley to unseat them.
Also, health care operates in a highly regulatory environment with its complex interactions between patients, health providers, and insurers. For example, Amazon has taken interest in online pharmacies. Look at the complexity of entering the pharmacy world:
- The Food and Drug Administration regulates drugs.
- Health insurers try to rein in their drug costs.
- Drug manufacturers set their own list prices.
- Pharmacy managers coordinate deals between health insurers and drug manufacturers.
- Consumers are trying to traverse through all this complexity and get their medications at the lowest prices.
In contrast, the benefits of the tech giants’ entrance into the healthcare industry cannot be overstated. Electronic medical records, mobile phones, and health assisting apps have slowly received widespread implementation by the healthcare world. The conglomeration of the two worlds has been at play for several years now. And yet, health care is still incredibly timid in its use of information and consumer technologies.
With the huge amount of money at stake in health care, the tech world’s disruption of this industry could be just what the doctor ordered. Imagine companies like Microsoft adding their knowledge, expertise, organizational skills, operational know-how, and other advantages to the healthcare industry. Patients will receive much better care at a fraction of the cost.
Can They Just Get Along?
Whenever the new kid shows up on the block, there is always fear, mistrust, and jealousy that is felt throughout the neighborhood. In order for tech companies to succeed in the healthcare market, they will ultimately need to forge relationships with professionals who are deeply rooted in this tangled system.
But when push comes to shove, they both can learn from each other. Case in point: Microsoft’s Glabella, which will try to replace the traditional cuff monitor with eyeglasses for tracking blood pressure. The sensors on this new product have only been shown to be accurate for taking the systolic pressure. For optimum accuracy, blood pressure should be measured by taking both systolic pressure and diastolic pressure.
According to the CDC: “The first number, called systolic blood pressure, measures the pressure in your blood vessels when your heart beats. The second number, called diastolic blood pressure, measures the pressure in your blood vessels when your heart rests between beats.”
While systolic pressure is commonly recognized to be more important than diastolic pressure, both readings are important. Systolic pressure is better at assessing your risk of having a stroke or heart attack. Diastolic pressure shows whether or not the heart is relaxing enough and can help doctors prevent future cardiovascular problems in a patient.
As Microsoft’s prototype medical device evolves, developing a way to measure both systolic and diastolic pressure is a perfect example of why the tech and healthcare people need to find common ground in the modern world.
Wrap Up
Consumers in general will benefit greatly from the excellence that companies like Google, Apple, and Microsoft can bring to the healthcare industry. And, most people will agree that this is one area that has not been well-organized for many years. Pharmaceutical companies are well-known for suddenly raising the price of drugs to ten times what they were for no apparent reason. With these tech giants in control, prices should be reasonable. They should stabilize. Care should be improved as well. And with wearable healthcare devices, people will be able to better monitor their health.
In the end, consumers will be the real winners here. For too many years, the healthcare industry has loomed out of control and missed opportunities to provide better care for patients. Their bottom line has always been profit over patient care. With these tech giants now pushing forward, we can expect all that to change.

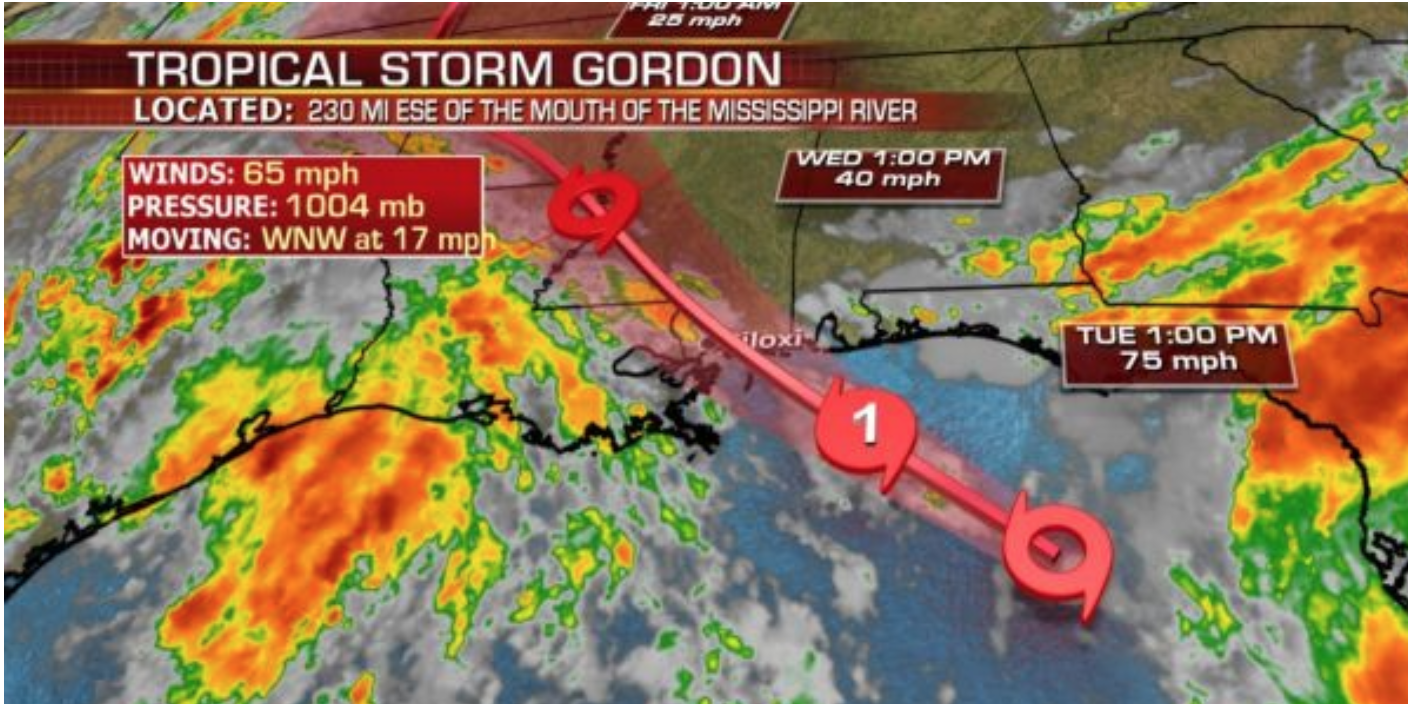






 We’ve reached what is considered peak hurricane season, and thus far the predictions have proven accurate. One of the measures of the lifetime and strength of storms is Accumulated Cyclone Energy. Thus far, the
We’ve reached what is considered peak hurricane season, and thus far the predictions have proven accurate. One of the measures of the lifetime and strength of storms is Accumulated Cyclone Energy. Thus far, the 



