Hurricane Florence strengthens to Category 4
Evacuation Orders Begin in the Carolinas
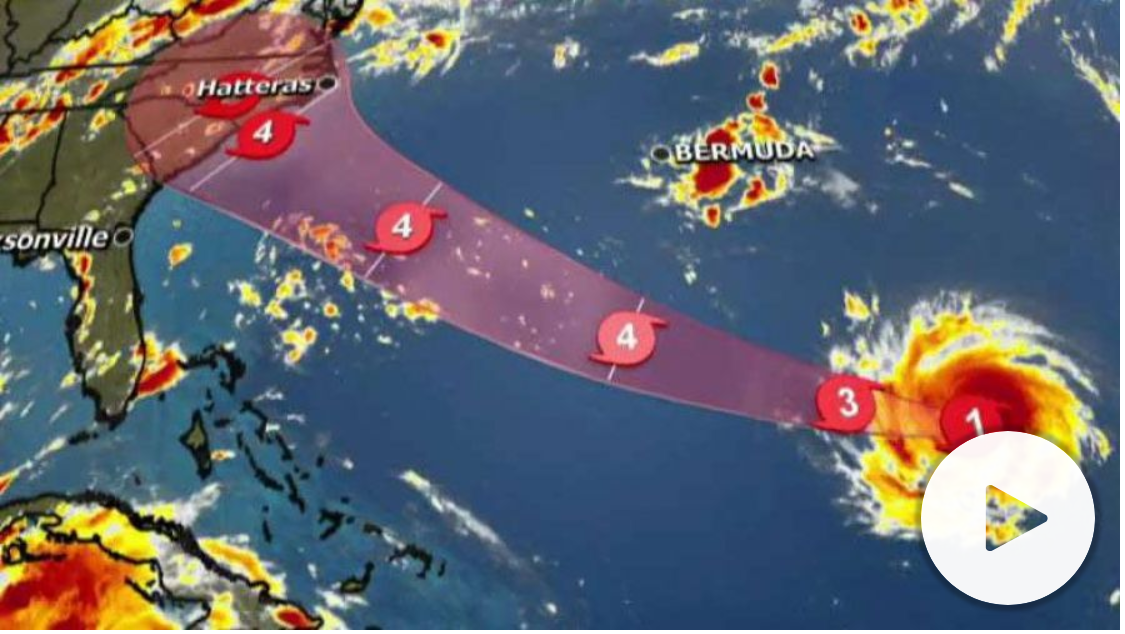
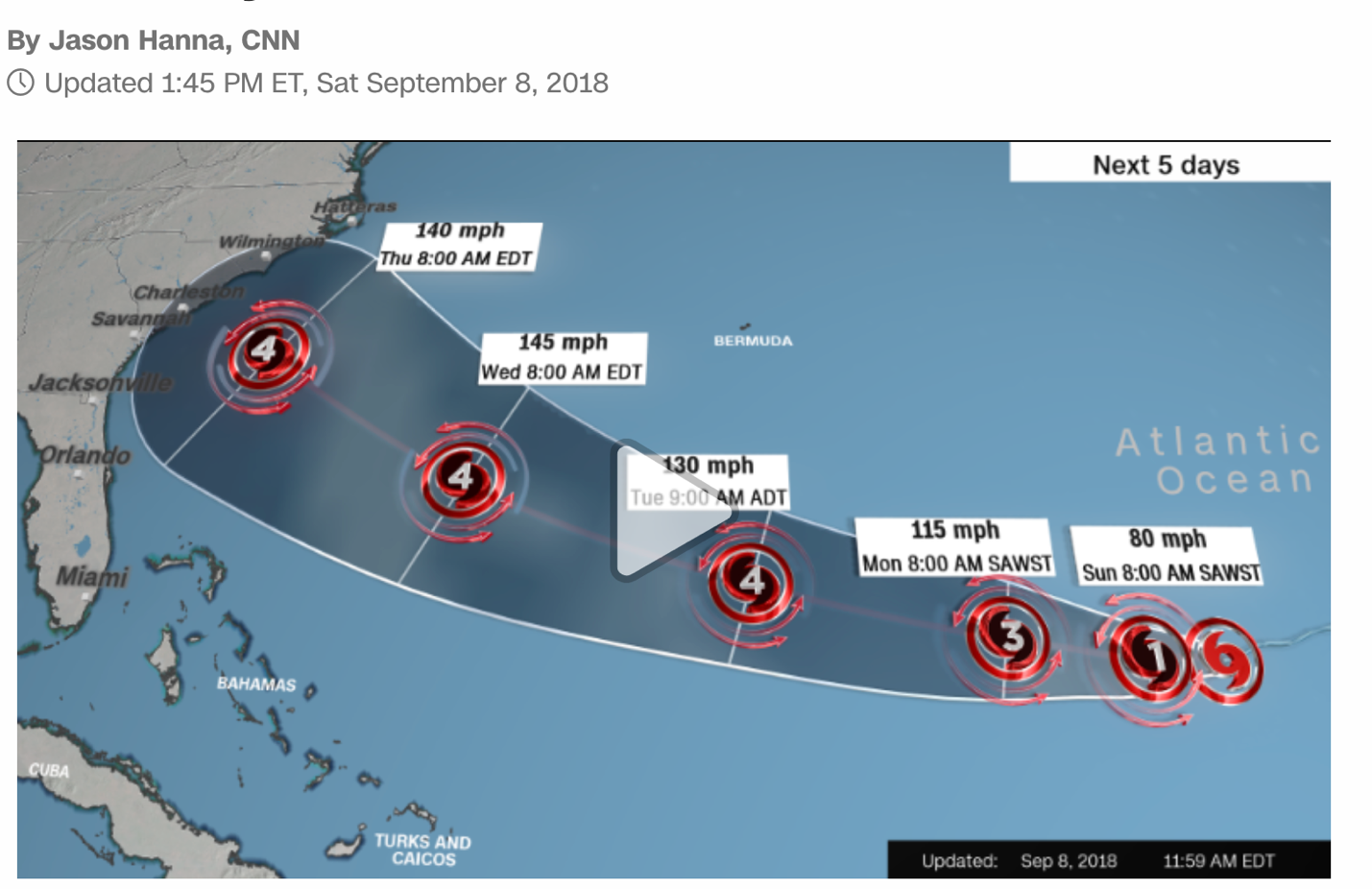
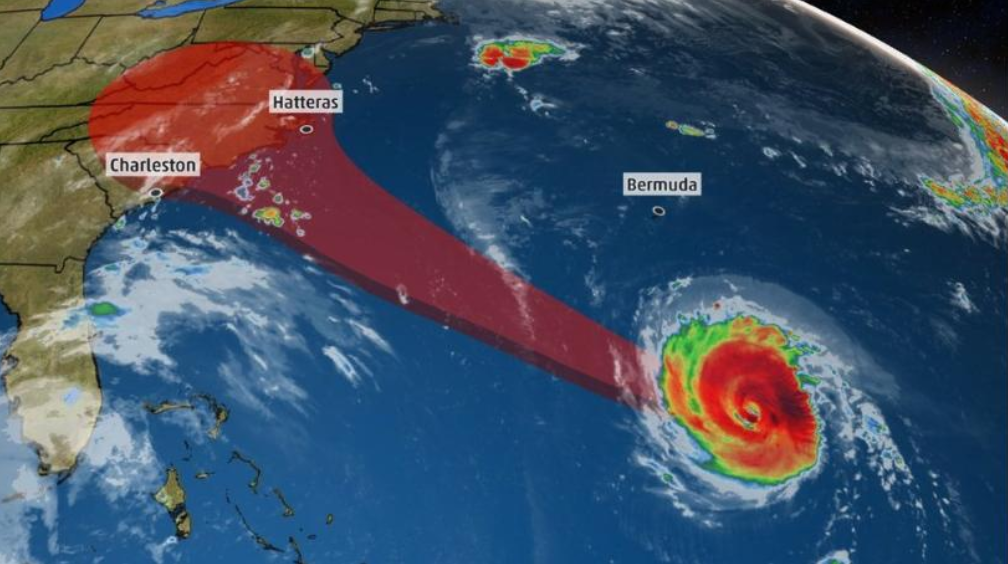
The National Hurricane Center is now saying that Florence has maximum sustained winds of 115mph, with gusts to 140mph. It is now a Category 4 storm and is expected to hit the Southeastern US coast on Thursday.
North Carolina, South Carolina, Maryland, and Virginia governors have declared a state of emergency and urged residents to be prepared by stocking up on the essential supplies of food, water, flashlights, and batteries.
N.C. Governor asks Trump for Federal Declaration
With Hurricane Florence setting its sights on the Carolinas, North Carolina Governor Roy Cooper has asked President Trump to declare a federal disaster. The Governor said on Monday, the federal declaration would allow for federal assistance and increase the state and local efforts in providing for a proper emergency response. Governor Cooper said he had a conversation with FEMA Director Brock Long on Monday.
Governor Cooper Says to Prepare for the Worst
The North Carolina governor also forewarned citizens in Hurricane Florence’s path to prepare to be without power for an extended period of time.
In a Monday Morning press conference, Cooper said, “When it comes to utilities, families need to be ready. They need to prepare to be without power for a while; that’s why we’re urging people to have their emergency kits and prepare for this.”
Currently leaving it up to local and county governments, Cooper also anticipates the other coastal communities in North Carolina to issue mandatory evacuation orders for residents and visitors just like Dare County and Hatteras Island have already done.
Military Bases are Preparing for Florence
In Norfolk, Virginia, the U.S. Navy has directed all working warships and submarines in the area to leave port in advance of Hurricane Florence. Both the Naval Station Norfolk and Joint Expeditionary Base Little Creek have said they have almost 30 ships currently planning evacuate as soon as possible.
With an extensive beachfront, Camp Lejeune is preparing for Hurricane Florence as well. The largest U.S. Marine Corps base on the East Coast, Lejeune is located about 50 miles northeast of Wilmington, North Carolina.
Historic Hurricane
If the hurricane hits as hard as predicted, Florence will be the most powerful to strike the area in three decades. Water could reach up to 15 feet high, and rainfall will move inland over the next four to five days.
The center of the hurricane is heading over the southwestern Atlantic Ocean between Bermuda and the Bahamas and some are predicting it to intensify into a Category 4 storm. With winds possibly reaching as high as 130-156 mph by Wednesday, it should reach the East Coast on Thursday or early Friday.
The last category 3 hurricane to hit the Atlantic Southeast Coast was Hurricane Fran in September 1996. Fran caused extensive damage and was the fourth major hurricane of the 1996 Atlantic hurricane season.
Category 4 Hurricane History in the Southeast
The deadliest and most powerful hurricanes to hit the Southeast Atlantic North of Florida were Hurricane Hazel. in September 1954 and hurricane Hugo in September 1989. Hazel reached the U.S. right around the border between North and South Carolina, registering as a Category 4 hurricane. Before reaching the U.S., Hazel killed more than 400 people in Haiti. It then belted Canada, categorized as an extratropical storm.
Hurricane Hugo was briefly a Category 5 hurricane crossing over Guadeloupe and St. Croix. It Weakened as it passed over Puerto Rico to a Category 3 hurricane and was downgraded to a Category 2 as it rematerialized in the Atlantic. But, just before it reached just the Charleston area it re-strengthened into a Category 4 hurricane, with 140 mph sustained winds.
Hurricane Florence News from Myrtle Beach
Myrtle Beach area residents have been asked to evacuate if and when Governor Henry McMaster gives the order. Myrtle Beach Spokesman Mark Kruea said for those who make the choice to ignore the order, “You take your own life into your hands.”
Kruea also said Myrtle Beach does not have “mandatory” the evacuation policy, but they strongly warn about the dangers if its citizens choose to stay.
Hurricane Florence News from Charleston, SC
Hurricane Florence’s path looks Charlotte and the city’s surrounding area will experience the impact of the Hurricane’s power.
Charlotte authorities are closely monitoring the Hurricane’s progress to help its residents be ready when Florence makes landfall and moves inland.
Hurricane Florence News from Wilmington, NC
Wilmington and all of Southeastern North Carolina area could easily be affected by Hurricane Florence and are encouraged to take precautions by local government agencies.
The University of North Carolina Wilmington (UNCW) announced classes are canceled and issued a voluntary evacuation for all its students as the storm continues to rapidly approach the Carolina coast.
Hurricane Florence News from Florence, NC
Damaging winds and flooding rain are very possible later this week as Hurricane Florence moves inland. Florence residents are asked to start thinking now about how they will prepare for Florence and be vigilant about watching the progress of the Hurricane.



 Air Canada recently confirmed a data breach occurred between August 22 and 24, affecting users of the Air Canada mobile app. The breach is just the latest in a string of cyber-attacks impacting mobile app users.
Air Canada recently confirmed a data breach occurred between August 22 and 24, affecting users of the Air Canada mobile app. The breach is just the latest in a string of cyber-attacks impacting mobile app users.