There’s a new Gift Card scam going around that has already cost consumers lots of money, frustration, and headaches. Here’s how it works.
You’ll get an email from a friend or relative asking you to go buy them a gift card. The email will say that your friend or relative has been busy or sick and unable to get to the store. Once you get the card for them, they’ll ask you to take a quick photo of the gift card code on the back and send it to them. Once you do this, they can cash out the gift card and you lose your money. It happens just that quickly.
Can You Help Out a Friend?
This scam has been working well for several reasons. Usually, the email comes from someone you know, maybe a sibling, parent, or aunt. Of course, you want to help them out, right? But one thing many consumers don’t realize is just how simple it is to hijack an email account. This is easy work for any hacker worth his salt.
For some reason, people just believe that the email is legit and never take that extra step of calling their friend or relative and just asking them, “Hey, did you send me an email about buying you a gift card?” That’s all it would take to avoid being a victim here.
Instead, most people will run down to Walmart or Target, buy the gift card, take the photo of the code on the back and think they’re doing a great favor for someone.
After you send the pic of the code back to the hacker, they will move very quickly to cash out the gift card and you’ll lose all your money. Later, of course, you’ll learn that your friend did not make such a request and now you feel silly for not double checking. After all, we should we savvier than that as consumers, right?
New Apps Make Scamming Much Easier
Unfortunately, these types of scams have been working well for many years. Plus, new apps like Raise make it easy to turn unused gift card balances into money.
Though victims do sometimes reach out to local police for help, this is actually not a crime. I know that most people are stunned by that news, but it’s true. Because you were a willing participant and you initiated the action with intent, no fraud was committed. So now you’re out the cost of the gift card and there’s really nothing you can do about it.
Just In Time For the Holidays
Authorities are warning consumers that this scam will be prolific all throughout the holidays. That’s why it’s so important to spread the word. Let your friends and family know that if they get a request like this from you or anyone, be sure to stop and call the person. Ask them if they really sent the email asking for a gift card. It only takes a couple of minutes to do this and it can save you $50 or $100 bucks.
Other Scams to Watch Out for During the Holidays
Hackers infamously took over the Rio Summer Olympics a few years back using social engineering to exploit the event. Though some were shocked, social engineering has been around awhile and is used every day to trick business owners. This scam costs Americans millions of dollars each year and hackers find new ways to make their tricks even more effective.
Phishing Scams
Used more frequently than any other, phishing scams have become so widespread that it’s difficult to get accurate results of the losses incurred.
PhishMe is reporting that these scams are growing by at least 65% per year.
Kaspersky Labs claims that during the first quarter of 2018, its anti-phishing system prevented more than 107 million attempts to connect users to malicious websites.
A Barkly reports shows that 85% of companies have fallen victim to this scheme.
How It Works
Phishing scams work relatively easily. It’s not rocket science, as they say. You get a legitimate sounding email that seems to be from your bank or credit card company. These emails often use fear and urgency to make victims take action before double checking the legitimacy of the email.
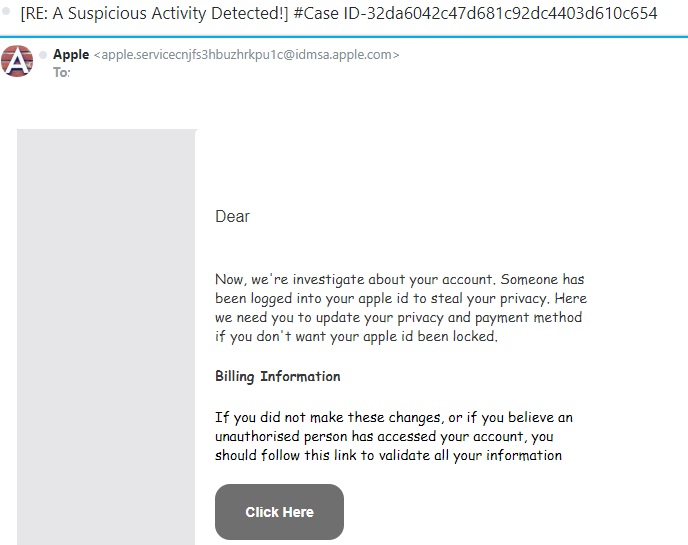
Below is an example. This scammer claims to be contacting you from Apple. If you check out the “From” address, you can quickly see that it’s not a legitimate Apple email account.
Another big clue is that words are misspelled and the grammar is very poor. You can tell that this email was written by someone (probably from Eastern Europe) who has very bad English skills.
NEVER click the link in a suspicious email like this one. Once you do, the cyber thieves can download malware or ransomware to your computer. They may also redirect you to a site where they steal your banking and credit card information. At the very least, they will steal your log-in information for your Apple account and then hijack it.
Final Tips
In order for consumers to avoid being a victim during the holidays, it’s important to watch out for these types of fraudulent activities. Never click a link in a suspicious email. Instead, open a new browser page and navigate to the website the way you ordinarily would. If there’s something wrong with your Apple account, a bank account or a credit card account, you’ll have a letter in your Inbox explaining what happened and what you need to do.
By using a little common sense and double checking when something feels suspicious to you, we can all avoid being victims this holiday season.










