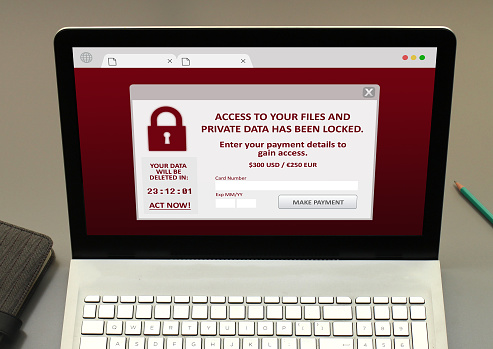
Everyone makes foolish mistakes. You’ve done, I’ve done it, and it’s all part of being human. But if that mistake affected your IT security, consider the ramifications it could have on your organization for being careless. For instance, a computer hacked or leak of sensitive data because a password was easy to crack. Luckily, these security problems don’t have to become a common occurrence and can get fixed easily.

What Are The Eight Foolish IT Security Mistakes to Avoid?
In no particular order, we’ve created a list of the most common IT security mistakes technicians see regularly. Also included are their recommendations to fix and avoid making the same mistakes again.
Mistake #1 – Using a weak password or not having one at all
Even with all the security warnings repeated continuously, people will always choose the same or a straightforward password to remember. It could be a birth date, the word “password,” a family pet’s name or the number sequence: 1-2-3-4-5-6. Then there are other individuals, that decide they don’t want a password, or they’ll get to it later, but later never comes.
- Recommendation: Consider using a password generator. When using a password generator, it can create a strong password in seconds. Currently, on the market, there is Dashlane, Keeper Password Manager, Password Boss, LastPass, and Sticky Password.
Mistake #2 – Writing passwords on sticky notes or slips of paper
This mistake follows the previous one and makes it extremely easy for anyone to access your account or device, especially if they got their hands on your password. It is common to find a piece of paper and jot down our passwords. Or worse write it down on a sticky note and attach it to the back of your computer monitor. In all reality, why do that? It’s like you don’t have a password at all because everyone knows where you stuck it.
- Recommendation: Stop writing down your passwords on paper. Consider using a password saver. Currently, on the market, there is Dashlane, Keeper Password Manager, Password Boss, LastPass, and Sticky Password.
Mistake #3 – Refusing to install antivirus protection or disabling it for faster computer speed
There continues to be this belief that antivirus software is not needed, especially for those individuals and companies that own and use Apple/Mac devices, but this is simply not true. Yes, it can be frustrating when your computer slows down while software is running.
- Recommendation: Consider using an anti-virus program that won’t’ slow down your computer. Currently, on the market, there is Avast, AVG, Kaspersky, Bitdefender, and Check Point Zone Alarm.
Mistake #4 – Taking unnecessary risks with email and blindly trusting the sender
This mistake includes opening email attachments from unknown sources or people you don’t know. Or worse responding to these individuals and sharing highly sensitive information (such as credit card numbers or passwords). When you open an email with an attachment, and you don’t know who the sender is, leaves you wide open to a malware virus or your computer hacked. Please be mindful; when sharing personal information, always remember, doing so could place you, your business, and your client’s information vulnerable to identity theft.
- Recommendation: From this point forward, no longer send sensitive information or data through an email. Consider using a tool like Google Drive. You can then send the data as a link which requires the recipient to log in first before they can access the file.
Mistake #5 – Walking away from your computer and not locking the screen
Eavesdropping continues to be an overlooked security issue and risk. When you get up from your computer and walk away, who has taken notice, that could potentially gain access to your account? What might happen if you forgot to close the bookmarked tabs in your browser, to step away, and on those tabs were your online banking account or your company’s bookkeeping system? With an open unlocked screen, you’ve given anyone full access.
- Recommendation: Always lock your computer before leaving it. On most keyboards, you will see the Microsoft Windows key. Press and hold it down while you press the letter “L” key, and your screen instantly locks. You can also preset your computer to automatically close after a specific amount of time passes (one minute, five minutes or 10 minutes).
Mistake #6 – Not installing the application and operating system patches or updates on time
Operating system updates and patches are crucial and vital in protecting your computer from evolving threats. Mainly, these updates and patches keep your computer healthy. Next time, before you hit the “not now” or “ask me later” button, reconsider.
- Recommendation: When prompted, always install the updates and patches when notified. Better yet, at least once a week, deliberately check for updates and patches. If you’re unsure where to begin, contact us or send us an email and we will help you.
Mistake #7 – Putting off having a reliable, stable, and well-tested cloud storage backup
It’s going to happen. Servers will fail, and computers will crash. It’s not if, but when. Not considering what a lifesaving tool, cloud computing offers, is like signing a death warrant on your files. Besides getting hacked, there are other reasons servers go down, i.e., age, fire, flooding, natural disasters are just four everyday occurrences.
- Recommendation: Seek out an IT company that hosts cloud storage services or is a vendor partner with a large cloud computing company. Do take the time to read and understand the SLA they present to you before you sign their contract.
Mistake #8 – Allowing personnel that is untrained, or not certified to secure your IT systems
Unfortunately, employees will be the most significant security threat a business faces. Most of the time is it not intentional, but human error and lack of training that usually causes the problems. It may seem convenient, but not everyone is an IT expert or specialist. IT security has many moving parts, and if one piece isn’t correctly set up, your system remains vulnerable.
- Recommendation: Allow your employees to do what you hired them to do. But when it comes to your IT system, consider hiring an outside IT services provider.
Did you find this article informative? If you liked this one, check out our other content we think you’ll find interesting.