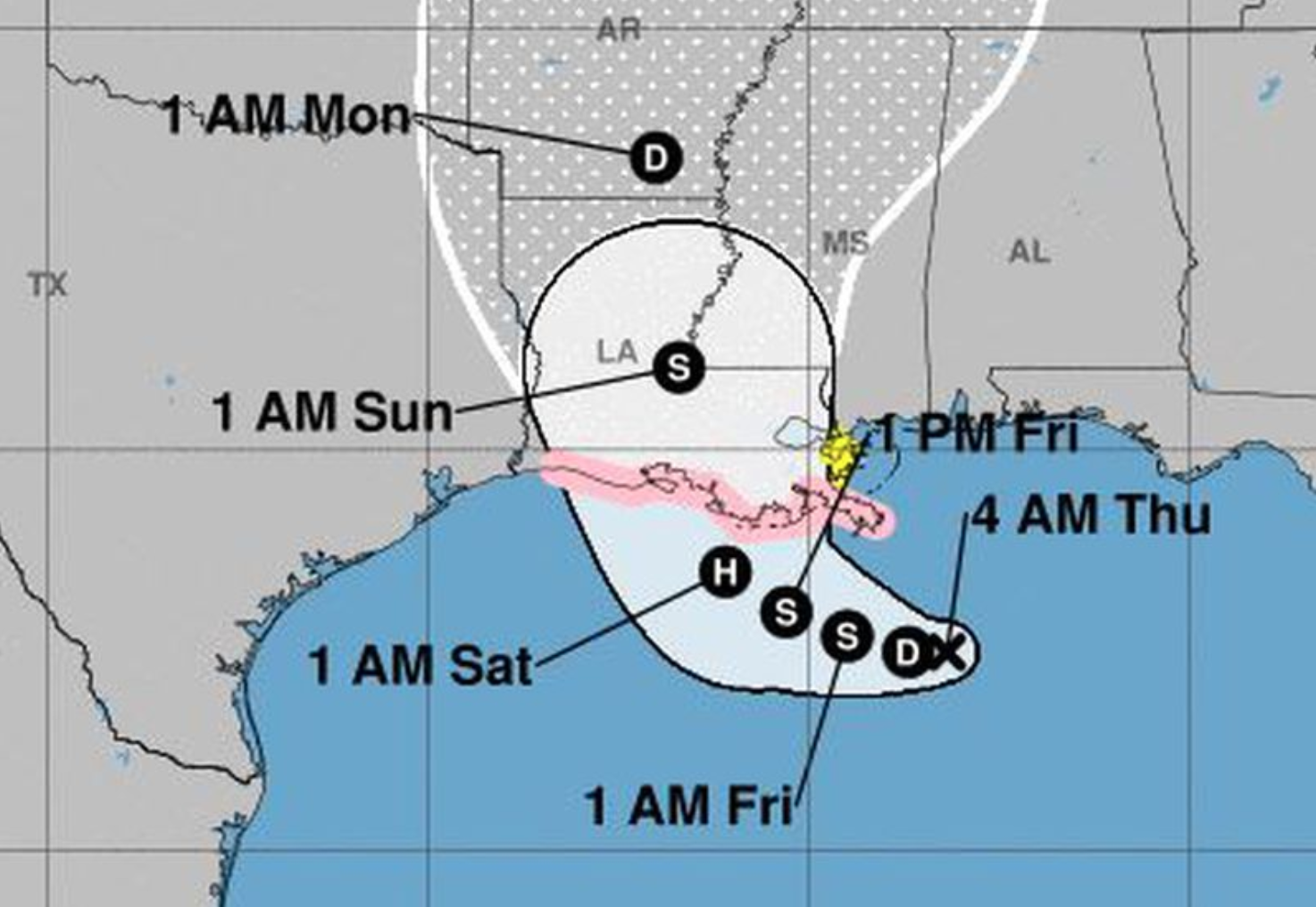
Tropical Storm Barry is expected to hit Louisiana and Texas in just a few days – what steps can you take right now to make sure you’re prepared?
As of yesterday, parts of coastal Louisiana have been put on hurricane watch in anticipation of what could be the first tropical storm system to make landfall in the US this year. Watches apply specifically from the mouth of the Mississippi River and west to Cameron, LA.
Tropical Storm Barry is expected to form in the Gulf of Mexico and develop into a hurricane by this Saturday, at which point it is likely to head through Louisiana and the upper Texas coast.
If you’re located in an area for which a watch has been issued, what steps can you take right now to protect your business?
Develop A Hurricane Preparedness Plan
Your hurricane plan should be carefully constructed and written down for reference and review.
Your plan should put forth policies and procedures regarding employee safety, business continuity, and contingencies that can be activated if your business’ facilities are damaged.
There are three key steps to an effective Hurricane Preparedness Plan:
Protect your property.
While so much of disaster recovery these days is focused on data continuity, it’s important to remember that your facilities are a resource as well, and they should be protected.
- Make sure your windows have proper shutters or are boarded up with plywood to keep them safe from airborne debris.
- Inspect your roof prior to each hurricane season to make sure it’s in good shape.
- Assess whether there are any aging branches or trees that could fall and cause damage during a storm. If you’re unsure, have an arborist check it out for you.
- Bring sandbags to areas that could be affected by flooding.
- Secure heavier objects, including bookcases, shelves, filing cabinets, computers, etc.
- Secure utilities, and raise them off the ground if necessary to avoid flood damage. Prior to the hurricane reaching your area, make sure they’re all turned off.
- Relocate any fragile or valuable items to less dangerous areas, if possible.
Protect your documents.
Once all your physical assets are taken care of, don’t forget about your business documentation.
- Make sure you have a backup of info on important business contacts.
- Backup documents that are not easy to reproduce or acquire in the event of water damage – insurance and legal contracts, tax files, etc.
- Keep as much of your documentation as possible in waterproof containers.
Maintain a checklist of survival resources.
Lastly, you’ll want to make sure you have an inventory of all the hurricane-specific resources you’ll need.
These are the types of items you won’t be using otherwise year-round, and so, when you do require them, you don’t want to realize you’ve forgotten something.
-
- Independently powered radio/TV
- Three-day supply of non-perishable food for as many employees as you have onsite (including 1 gallon of water per person per day)
- Blankets, pillows, cots, and chairs
- First Aid supplies
- Flashlights (and additional batteries)
- Toolkit
- Whistles and/or signal flares
- Tarps, plastic bags, and duct tape
- Cleaning supplies
- Smoke alarms and fire extinguishers
- Electric generator
- A backup supply of gas and additional jerry cans
- Cash, credit cards and ID
- Emergency contact info
Don’t forget to brief your employees – your hurricane plan should not be written and then left on a shelf. Every employee should be familiar with your procedures and plans to handle any future emergencies. Hold a meeting where your plan is reviewed, roles are assigned, and your staff can ask questions.
Remember – without comprehensive disaster recovery planning, you’re left vulnerable to any and all emergency situations, whether it’s a major meteorological event like a hurricane, or common — and still unpredictable — power outages. Consequences include:
- Permanent data loss as onsite copies of your data are destroyed
- Severe downtime as your business scrambles to replace hardware and get up and running again
- Major financial damages, from the cost of lost business to the cost of replacement hardware and more.
There are still a few days until the hurricane is expected to hit – follow these steps and develop your plan now to make sure you’re prepared.










