Accidentally deleting a file or folder was once something that could ruin your entire day, week, or month even — maybe even your career. All that work put into it. Countless hours put into it. And then: gone. Fortunately for those of you using Microsoft OneDrive for professional, personal, or academic reasons, there may be a way to retrieve and restore files or folders that were deleted. The same is true if your files or folders were overwritten, corrupted, or infected by a virus or malware. Depending on your subscription, you may have two methods to recover files: (1) restore files from the Settings page; or (2) restore files from the Recycling bin.
Files or Folders Recovered Using Settings
From your OneDrive website, you will want to follow the next steps in order.
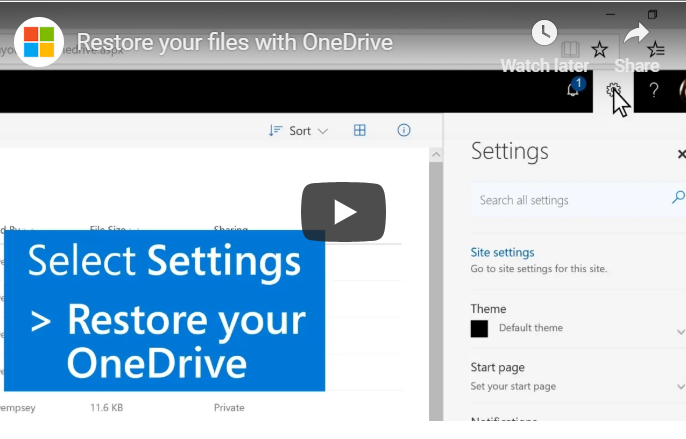
- Select Settings, which is the gear symbol in the upper right corner of the page — usually between the bell indicating notifications and the question mark for help.
- From the Settings sidebar, scroll down until you see Restore your OneDrive.
- The Restore your OneDrive page will open. Under Select a date, use the dropdown menu to select your option: (1) One week ago; (2) Three weeks ago; or (3) Custom date and time. If you choose Custom date and time, you will be provided with a chart. Simply slide the bar to indicate the days.
- Click the Restore button.
- All your files and documents from that time period will be restored.
If this option does not seem to work, there is another way to recover deleted files or folders.
Files or Folders Recovered Using the Recycling Bin
From your OneDrive website, follow these steps.
- In the navigation pane, select Recycle bin.
- The Recycle bin will generate a list of files and folders. If you use a work account, you have only one option for file recovery, but if you use a personal account for work, you have two options.
- For work and personal accounts, simply select the circle checkbox to the left of each entry you want to restore. When you select the circle check box, the header will change. Once all entries are selected, click on the Restore button in the new header.
- For personal accounts, you can also restore all items at once by clicking on the Restore all items button in the original header.
Things to Consider about Recovery of Files or Folders
Keep in mind that you can only recover files or folders in the Recycle bin so long as the files or folders have not been permanently deleted. Typically, files only live in the Recycle bin for 30 days for personal accounts or 93 days for business accounts — unless the administrator for business accounts changed the setting for a shorter or longer period. Once the time limit is reached, the files are automatically deleted. Files can also be automatically deleted within three days if the Recycle bin is full, at which time the oldest items are deleted first.
It is also important to note that if you want to restore a file to a specific version, File Restore cannot do so if version history was turned off. It is a good idea to always keep version history on while you work.
In summary, when using OneDrive, you have the potential to restore a file or folder that has been accidentally (or in some cases, intentionally) lost. The key is knowing the functions of your Microsoft subscription. Need more tech tips? Return to this blog. New tips for your OneDrive subscriptions and other tech needs are posted regularly.