Improving Data Analysis with the IF Function in Microsoft Excel
Have you ever wondered what the IF Function in Microsoft Excel actually does? Here we explore a few top tips for making it save you time while evaluating data.
There’s no doubt that Microsoft Excel is a robust program. Companies all over the globe utilize this application to analyze, track, and otherwise organize data in an easy-to-read format. But how much do you know about it and the various features that are available? And are you taking the right steps to ensure you’re looking at your spreadsheets in the most efficient manner possible? Here are a few of our tips and techniques to help you save time and improve your data analysis by using the IF Function in Microsoft Excel.
Tip #1: Understand What the IF Function Actually Does to Help Your Workflow
The first real step in making sure you’re using Microsoft Excel’s IF Function appropriately is to understand what it actually does. The IF Function tests whether a condition is true or false, and then performs an action. These actions can be calculations, data entry, or something closely related. The function is incredibly useful if you have large data sets or need to make significant changes, as it is a great way to save time in your workflow.
Tip #2: Creating the IF Function is Incredibly Easy
Creating the IF Function effectively starts with knowing the three parts: the logical test and then a value if true and a value if false. From there, all you have to do to make it work with your spreadsheet is to choose the data sets that you want to evaluate and determine what you want the true and false results to be. To do this, use the IF Function on the Insert a Function menu. Click okay and enter the conditions as you are prompted to do so on the screen.
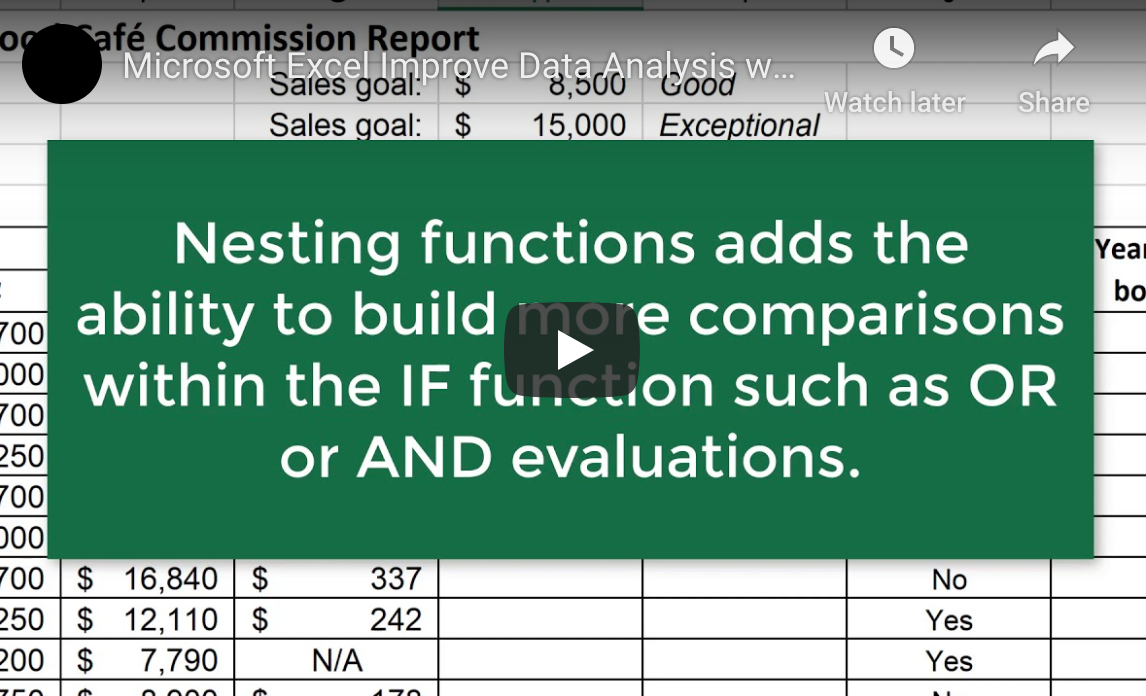
Tip #3: Knowing How to Nest Functions
It is possible to use multiple IF Function formulas at the same time. In some cases, you might have multiple different possibilities or different levels of data that you want to compare. That’s when knowing how to nest multiple IF Functions becomes important. Nesting functions adds the ability to build more comparisons within your formulas instead of having to complete them separately.
Tip #4: Adding AND and OR to Your Functions
You can also add AND and OR to your IF Functions to make the results much more specific. While this is technically part of understanding how to nest functions, knowing how to do this is an effective way of utilizing the IF Function in a more efficient manner. An example of this is comparing two columns of data: one showing the amount of sales and one determining if an employee has completed training. By adding AND or OR to your IF Function, you can show a specific result, such as those employees that hit a specific sales goal and finished the training program you provided. As you can see, this can be a really easy way to get the information you need without having to spend a ton of time scouring through your entire spreadsheet.
Tip #5: Using Range Names to Make Data Easier to Sort
Range names are essentially a stored label that allows you to identify a range of one or more cells. They are incredibly useful for navigation, formulas, and even printing off specific parts of your spreadsheets. For use with the IF Function, you can utilize data ranges to save time when you’re working on a specific block of values as it allows you to use that range name instead of specific cell names. Range names can have letters, numbers, or an underscore, but cannot have spaces. And they are not case-sensitive, but title case is recommended for ease of viewing.
Tip #6: Remembering to Use Quotations with Text Strings in Your IF Function
Using the IF Function is an incredibly easy way to add text to a specific cell when certain criteria are present. However, you do need to remember to use quotations around your text strings in your IF Function formula. Failure to do this can really mess up your data set and make the formula not work correctly. Should you have a problem getting the IF Function to work for you, this is one of the first things you need to check.
Tip #7: Changing Text with Conditional Formatting Based on Your Result
Not only can you add text or insert a formula with the IF Function, but you can also change text visually with conditional formatting based on your result. It can be done automatically and setup within Excel under the Home tab. Examples of this option in use include turning a specific number bold and red if it does not meet the criteria of your IF Function, or highlighting it in yellow if it does meet certain requirements.
Conclusion
Microsoft Excel is a great way to analyze and interpret datasets. The IF Function allows you to do this in an easy-to-read and simple manner while saving you tons of time in the long run. These quick tips are a great way to skip complicated formulas and really make your spreadsheets work for you.
![]()